Video - How to buy an ATM - Hacktivity 2017
A video of my talk about the process of buying and hacking an ATM

Given the high level of interaction we all have payments every day; how is it that we don’t know more about payment technologies? I want to change that. I am going to shed a little light on payments for everyone. So in this article, the first in a series, I’d like to explain how payment systems work. And because I specialise in security I will also talk about the security risks associated with payments. Just to be clear I’ll be talking about regulated money and won’t be covering cryptocurrencies. I’ll be using words which are common in the payment industry, you’ll become familiar with these as we progress.
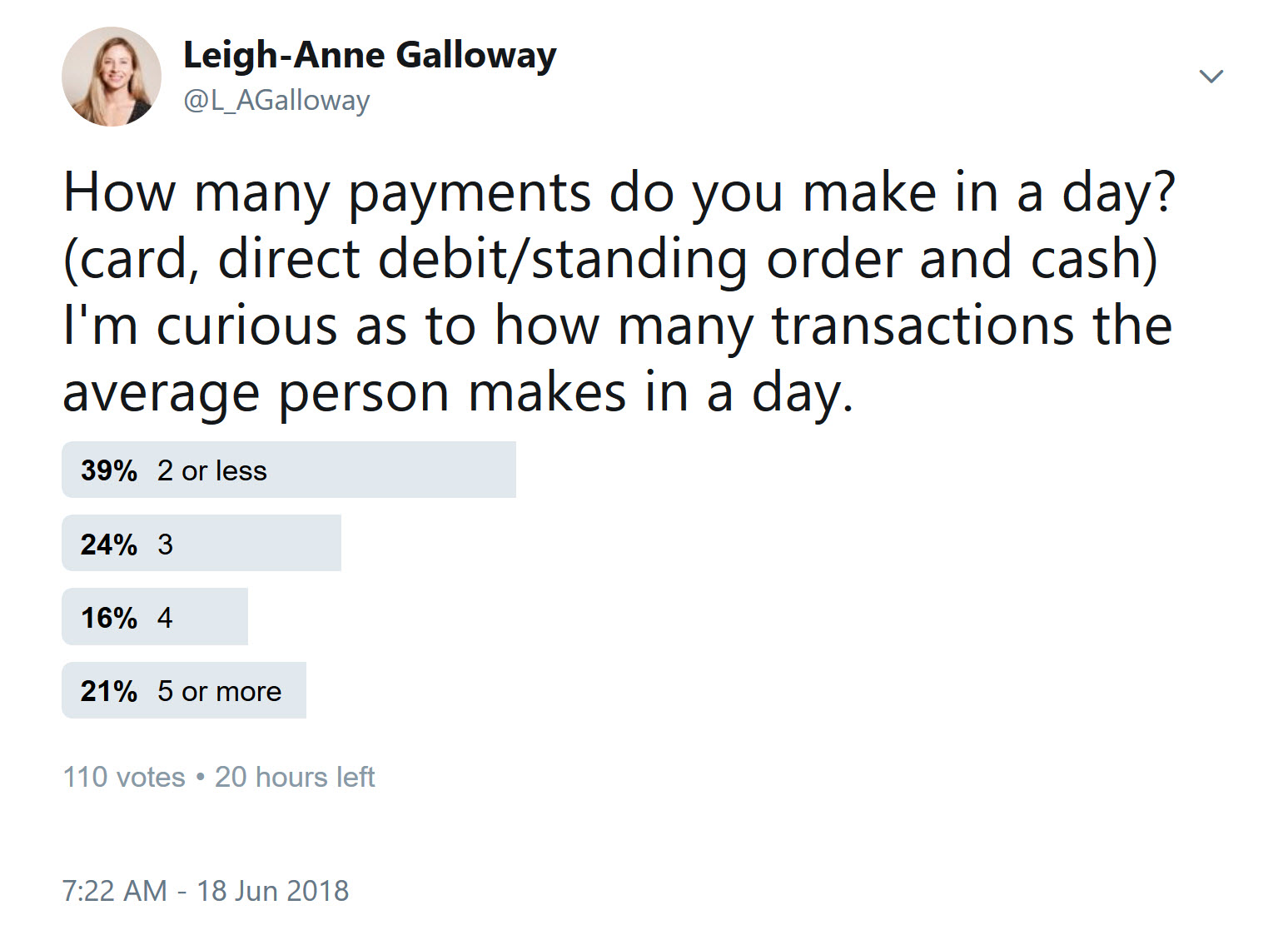
We interact with payment technologies every day. So much so, that most of us take it for granted. In any given day I will use my cards to pay for transport on the London underground (contactless), buy lunch (chip & pin), and pay for groceries (another contactless payment). I might even buy something online (card not present transaction). During the same month, I will use a taxi, withdraw cash from an ATM in at least one country and have several payments go out of my bank account for bills (standing orders or direct debits). I had made 106 transactions in the last month alone. That’s an average of 3.4 transactions per day for the last calendar month!
I dug a little deeper and asked the internet, how many transactions does the average person make in a day? The results are very interesting, showing a wide range of payment interactions. It’s important to understand that there are many factors which influence this number, which are outside of the scope of this survey. Factors such as where you live, how often you travel and the job you do, will affect this number. What about you, how many transactions do you make a day?
How many payments do you make in a day? (card, direct debit/standing order and cash) I'm curious as to how many transactions the average person makes in a day.
— Leigh-Anne Galloway (@L_AGalloway) June 18, 2018
Firstly, I want to introduce you to the payment ecosystem:

When you look at this image, it’s hard not to feel overwhelmed! Just like an eco-system in nature, this is made up of all of the components within payments that interact with each other and depend on each other. This includes card brands, banks and payment methods. In its essence the payment eco system contains many different individual payment systems. A payment system facilitates the transfer of funds between one individual and another individual or organisation. At the core of this process is a bank. This is true even for cash to cash transactions because they always originate from a bank.
It becomes much easier to understand when separated out into its individual components. There are three main components of a payment system, payment instruments, payment system operators and payment delivery channels. Payment instruments sit at the very end of payment systems and are mostly physical representations of money. These include cash, debit and credit cards, cheque’s, electronic transfers, standing orders and direct debits.
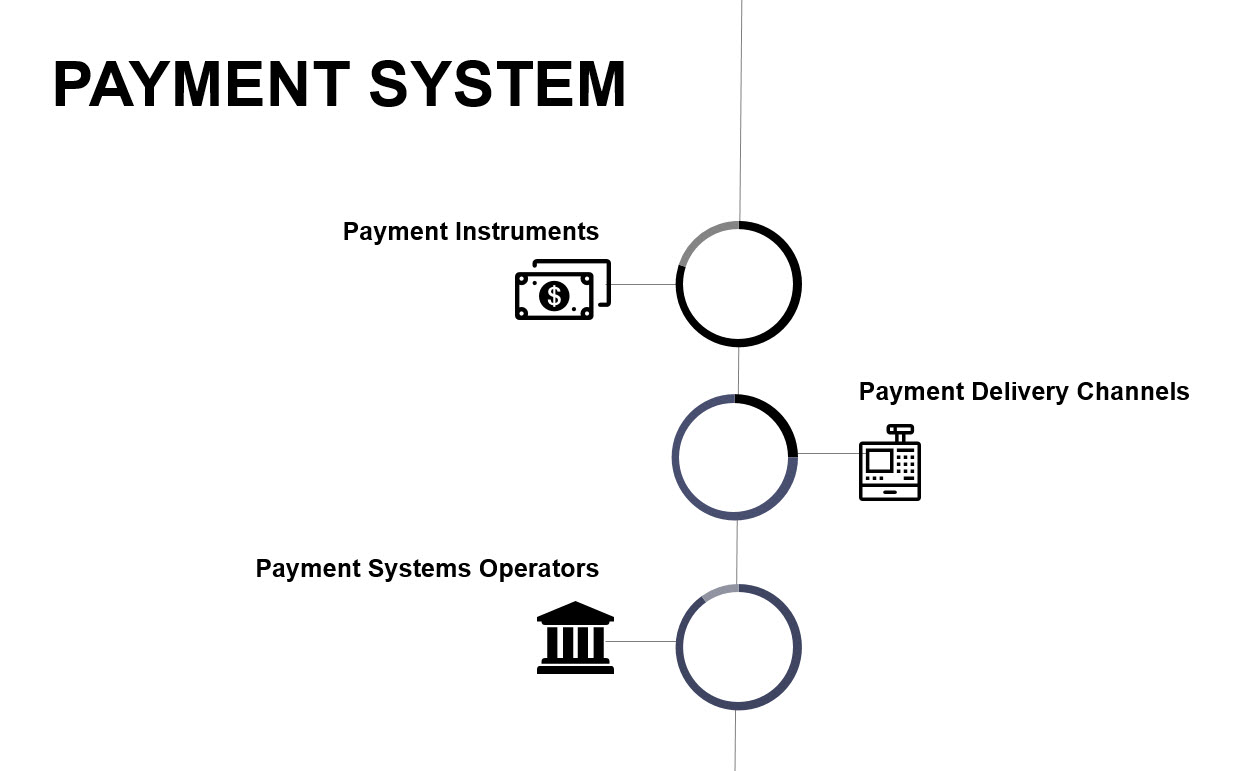
Next we have payment delivery channels. These facilitate the movement of money in and out of payment systems. These are ATM’s, Point of Sales terminals (POS), mobile Point of Sales Terminals (mPOS), mobile payments, payment gateways and bank branches.
Finally, we have payment system operators. Payment system operators make up the infrastructure of any payment system. They provide us with access to payment instruments and delivery channels. These include banks, clearing houses, card brands and other third parties such as PayPal and Google Pay.
In the next few articles, I’ll be focused on discussing the security risks associated with Payment delivery channels and payment instruments, but not payment system operators. This is because many aspects of payment systems operators are unknown, they function as a ‘black-box’ device. This means that it’s hard to understand how they work at a deep level without having the privilege of working in one of these environments. On the other hand, payment delivery channels and payment instruments are accessible to everyone and are essentially the front door to payment systems operators. For these reasons they are often the first focus for security researchers and of course criminals!