Video - How to buy an ATM - Hacktivity 2017
A video of my talk about the process of buying and hacking an ATM
Write up of the capture the flag (CTF) competition at 44Con 2018.

44CON takes place annually in London, UK. This year it took place from 12-14th September. This was my first time in attendance, both as a speaker and a CTF participant. I'm still a n00b to offensive security and to date had not participated in a CTF. I decided to give the 44Con CTF a try, because, well Steve (@stevelord) sold it to me in the opening ceremony ¯_(ツ)_/¯.

If you are not familiar with the format, a CTF or Capture the Flag, is a series of technical challenges. I had been warned before starting, that these challenges are nothing like the real world. Think of CTF challenges like puzzles. You may be tempted to apply real-world experience to these challenges, but they are often best solved by "thinking outside of the box".
The CTF consisted of eight parts: Trivia, Networking, Forensics, Crypto, Reverse-engineering, 44con (you have to be at the conference to complete this challenge), NCC (some tasks set by NCC group) and a scavenger hunt. Most of the tasks were made available straight away, but the NCC tasks only appeared around 30 minutes before the end of the competition. The Scavenger hunt was made available at the end of the first full day. I wasn't able to complete the NCC tasks as these were made available so late in the day. I also didn't understand until the end of the first day that the 44con challenge, which involved finding a suspicious usb key with a crypto wallet, was indeed part of the CTF. I thought this was a separate challenge.
The rules of the CTF are fairly straight forward; no cheating, which is obvious, and points are weighted by the complexity required to complete the task. The fewer teams that solve the task, the more points you receive for the task. This means that there isn't a benefit to being the first to solve a task.
I am providing links to the source files so that anyone can follow along.
Challenge 1 doesn't have a source file.
Challenge 2
Challenge 3
Challenge 4
Challenge 5
Challenge 6
Challenge 7
original version of Super Mario
Challenge 1
The first task under the Trivia section was called "The Problem is Choice". This involved finding the CVE which is shown in the 2003 film, "Matrix Reloaded".
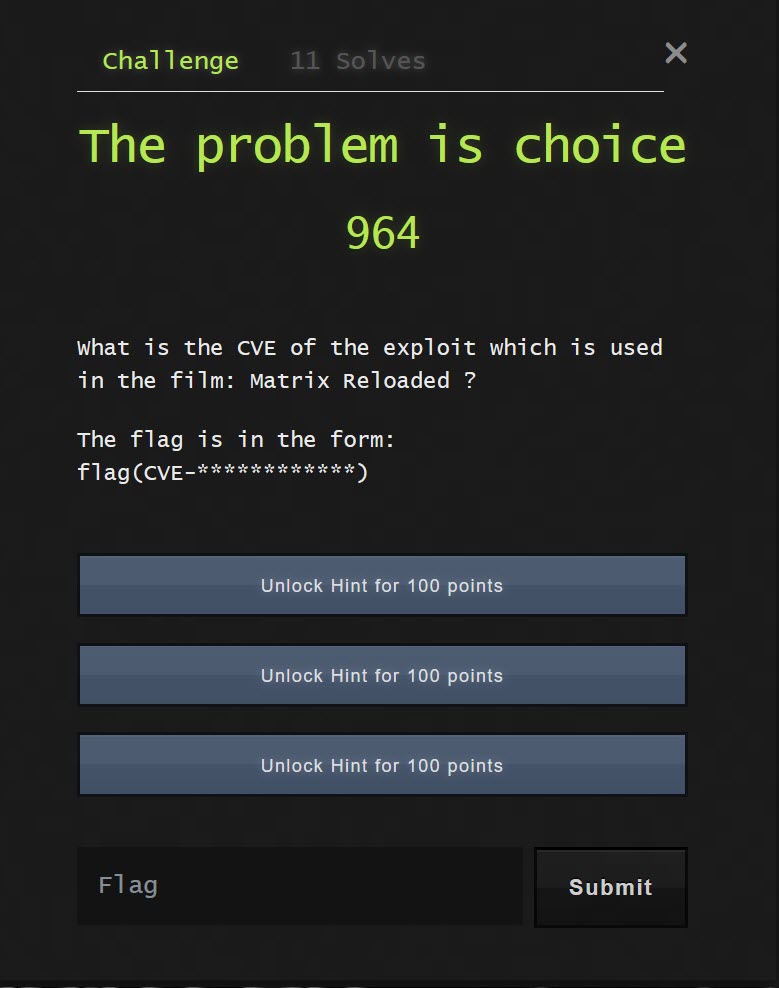
A bit of searching brings up the result, which is "CVE-2001-0144".
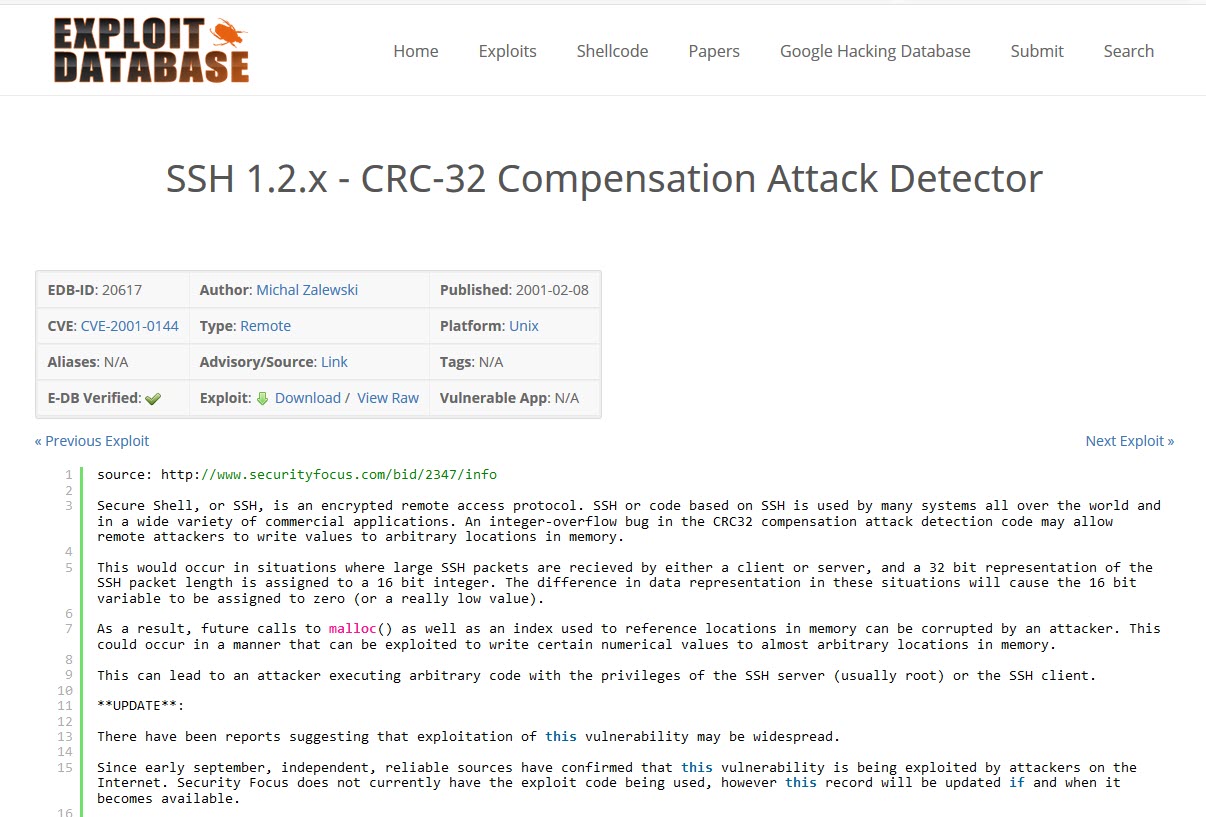
The flag follows the format "flag(answer)", so the answer is "flag(CVE-2001-0144").
The next task is called "Test flag, please ignore"... which is precisely what I did for a while ٩(^‿^)۶. The task asks you to see if you can find a code in the file, which is obfuscated in some way.
Challenge 2
If you unzip the containing archive, you find a file without extension called "TOP SECRET"
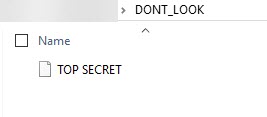
When I opened the file in notepad, I found a string which looks like it's ASCII encoded.
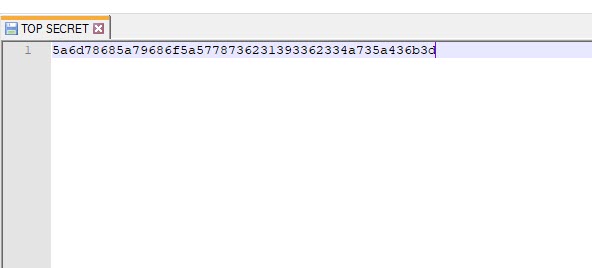
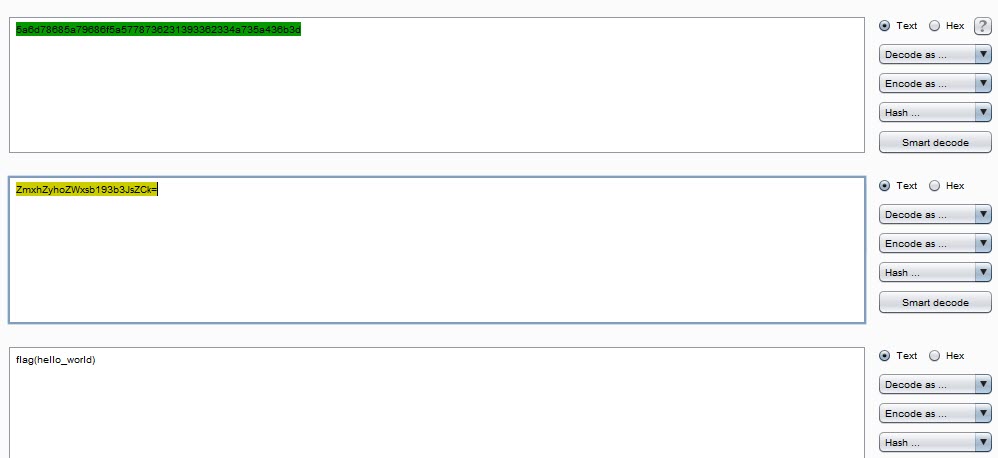
If you decode this string to ASCII, you get a string which looks like its Base64 encoded. If you decode this string, you get the flag, which reads "hello_world". There a lot of ways to decode this string, I chose to use Burp Suite's built in decoder.
Challenge 3
The third task involved extracting an IP address from an ARP request.
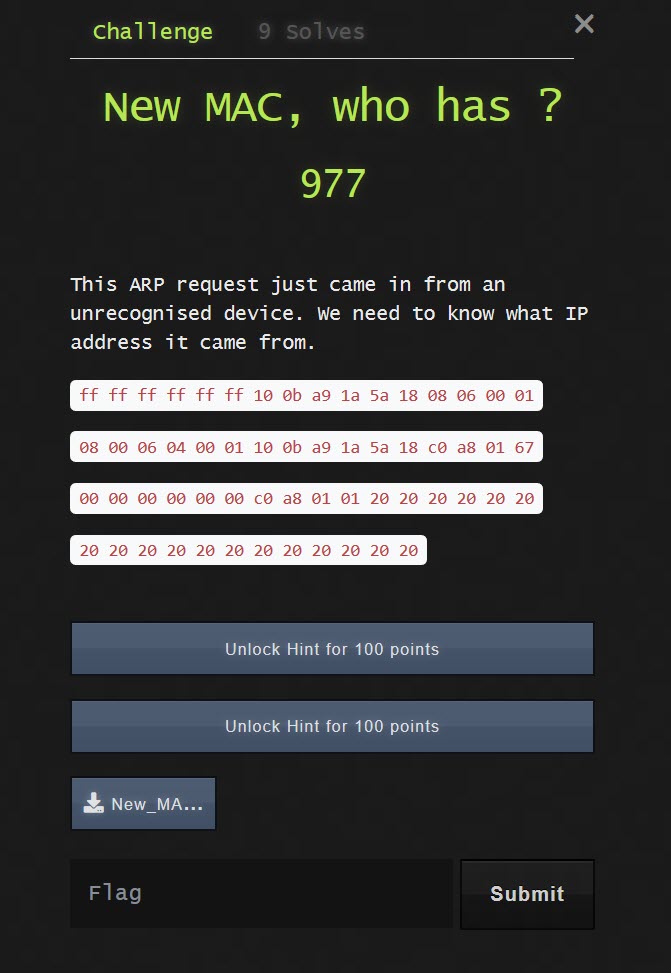
If we look at the contents of the file we can see a raw ARP request. This data is is hex.
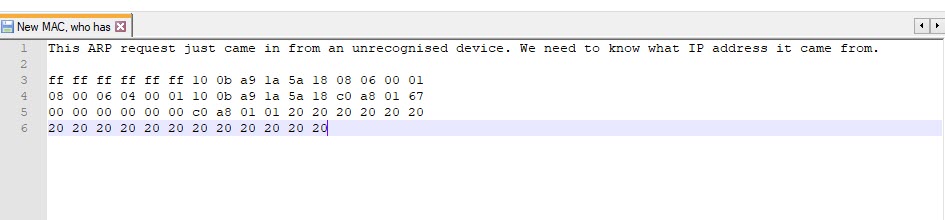
To determine the source IP that sent the packet we need to understand the structure of the packet and to convert the data from hex to an integer. This is a good resource which explains the data structure of IP based packets reading packet hex dumps
So if we take our hex dump and convert it to decimal:
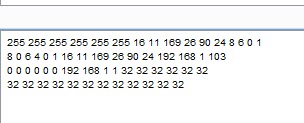
We can see that the source IP is "192.168.1.103" or "c0 a8 01 67". This is answer for our flag.
Challenge 4
Challenge 4 involves literally finding a needle in a haystack. For this challenge, you are provided with a pcap file, in which you must find a suspicious packet.
There are four hints for this challenge, which I think gives an idea of the complexity of this task. The first thing that I did was import the pcap into Wireshark and use the "Protocol Hierarchy" feature. This is a good place to start if you don't know what you are looking for. It shows you how much of each protocol is within the packet, and it can be helpful for identifying unclassified protocols.
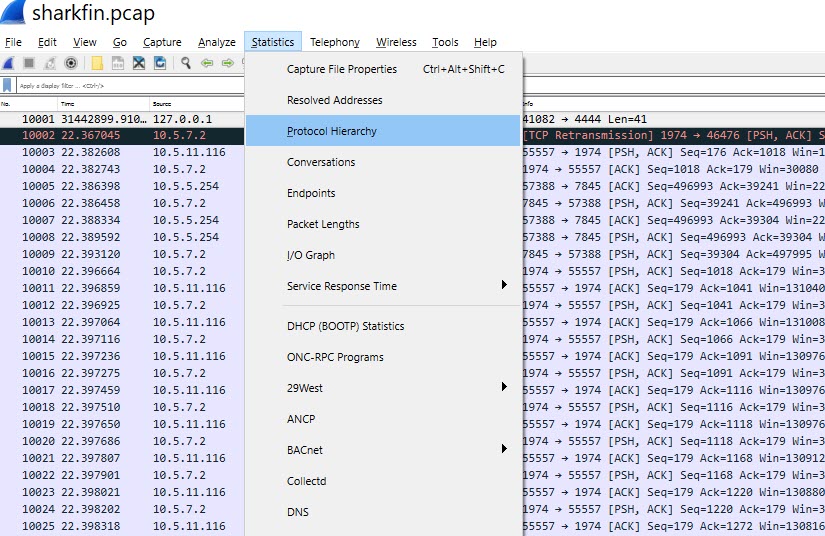
Here is the output of the "Protocol Hierarchy":
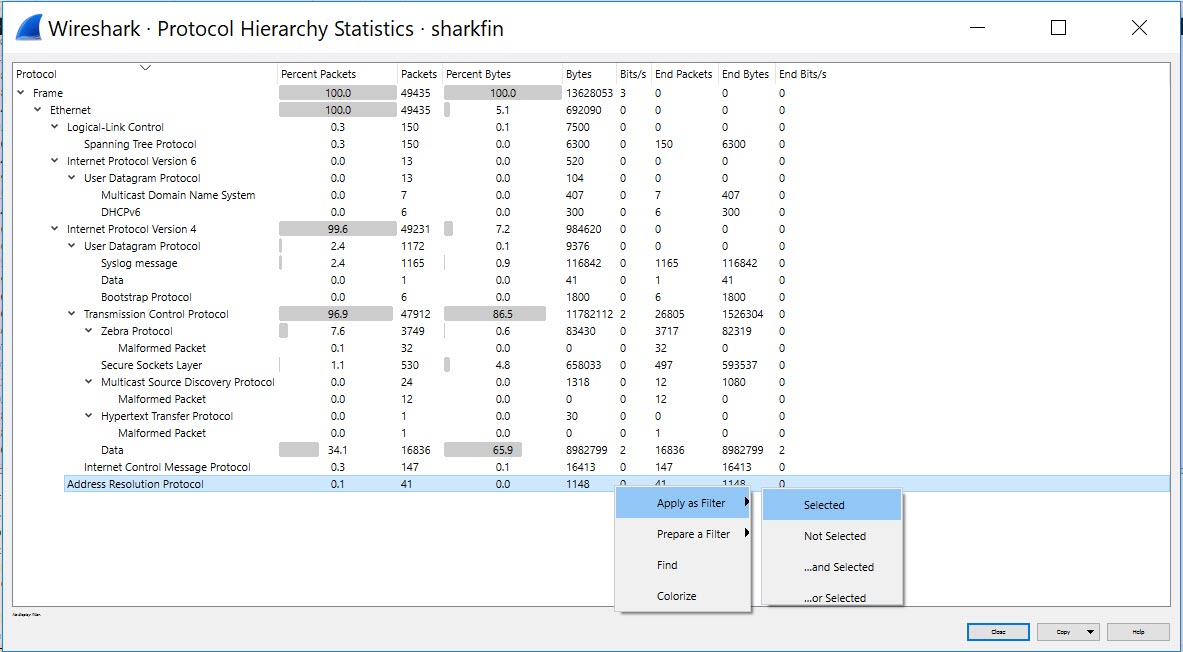
You can filter on a specific protocol from this statistics panel. I spent some time looking around the packet but nothing obvious stuck out. I decided to open the packet in network miner by Netresec.
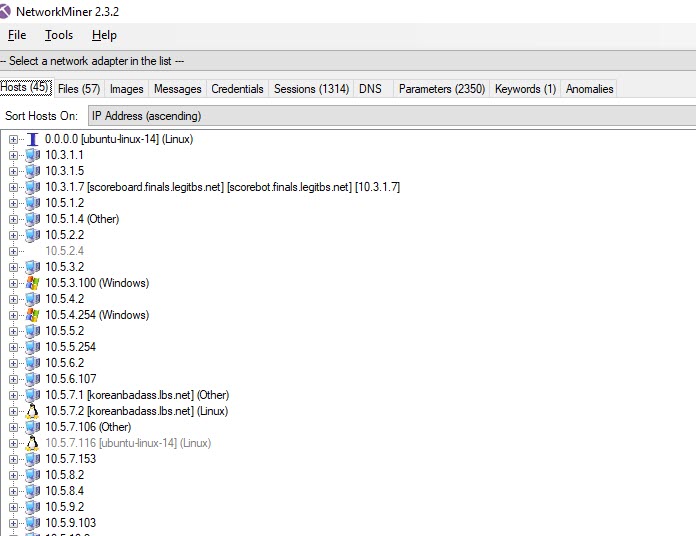
This is a great took which visually shows all the different communication between each host. It also allows you to carve out files a bit easier than Wireshark.
After a while of looking around using my real-world experience, I still couldn't find the flag. I decided to approach the task differently. Instead of analysing the pack for something that I would consider suspicious in the real-world, I decided to look for the flag. I took the string "flag" and converted this into ASCII and Base64, and searched for both of these terms in the packets.
I got a hit for the ASCII string!
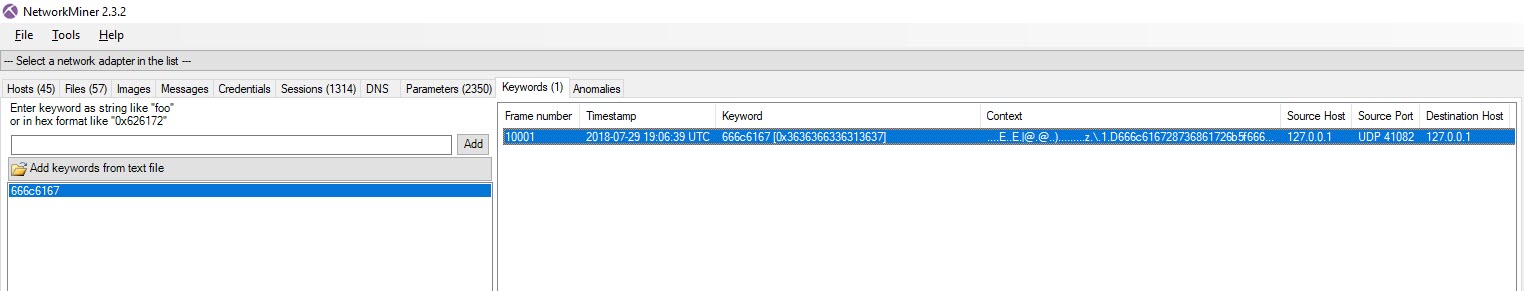
Here you can see the flag in a UDP packet. All we had to do is decode the rest of the flag. If we look at the packet, it does indeed look strange, 127.0.0.1 sending a UDP packet to 127.0.0.1
Heres the packet in wireshark:
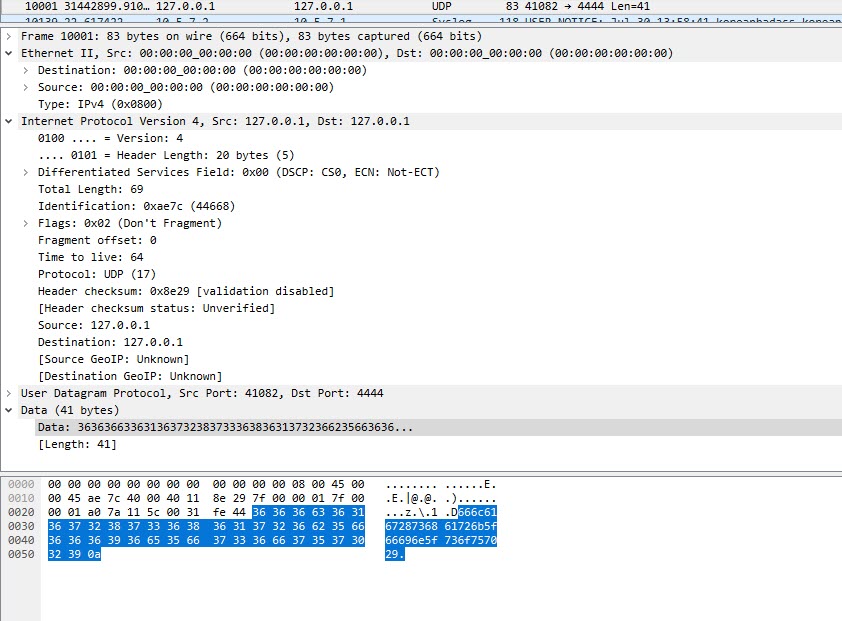
If we take the raw data from Wireshark:
Copy the raw bytes
Then decode this value to ASCII
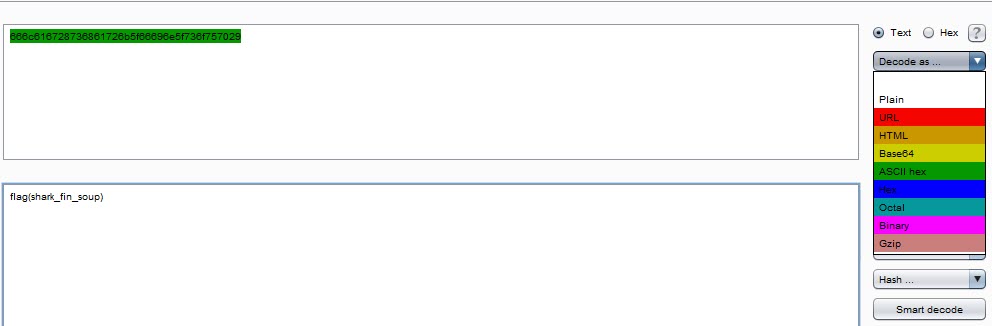
We get the flag "shark_fin_soup".
Challenge 5
In this challenge we were presented with an MP3 file. The challenge asks us to recover data from the file.
At first I looked at the file to see if there is a hidden file that needed carving out:
But this is in fact a genuine MP3 file and plays audio.

I have a fair amount of experience in forensics but so far this task was nothing like real world forensics! At this point I decided to get some guidance from other CTF write-ups. trailofbits is one of the best resources I could find online. In the guide it suggests that forensic challenges can involve "Steganography". This is a method of concealing a message in an image or other file type.
To find a hidden message in an audio file you need to use a spectrogram. I used Sonic Visualiser for this process, but there are other programs which have this feature available.
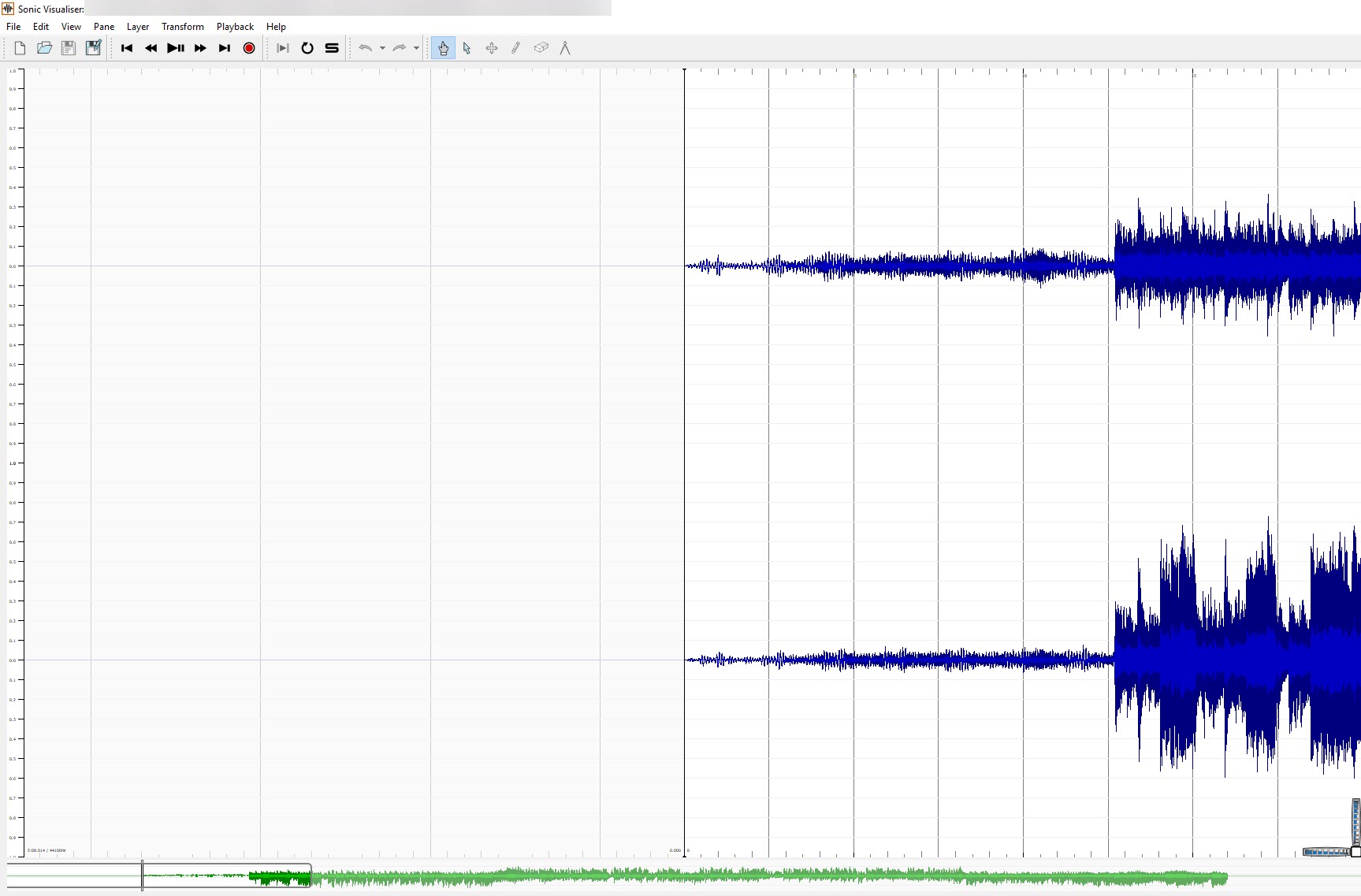
After opening the file in Sonic Visualiser, I was able to view the spectrogram for each channel individually:
Channel 1, didn't contain a hidden message. However, channel 2 did:
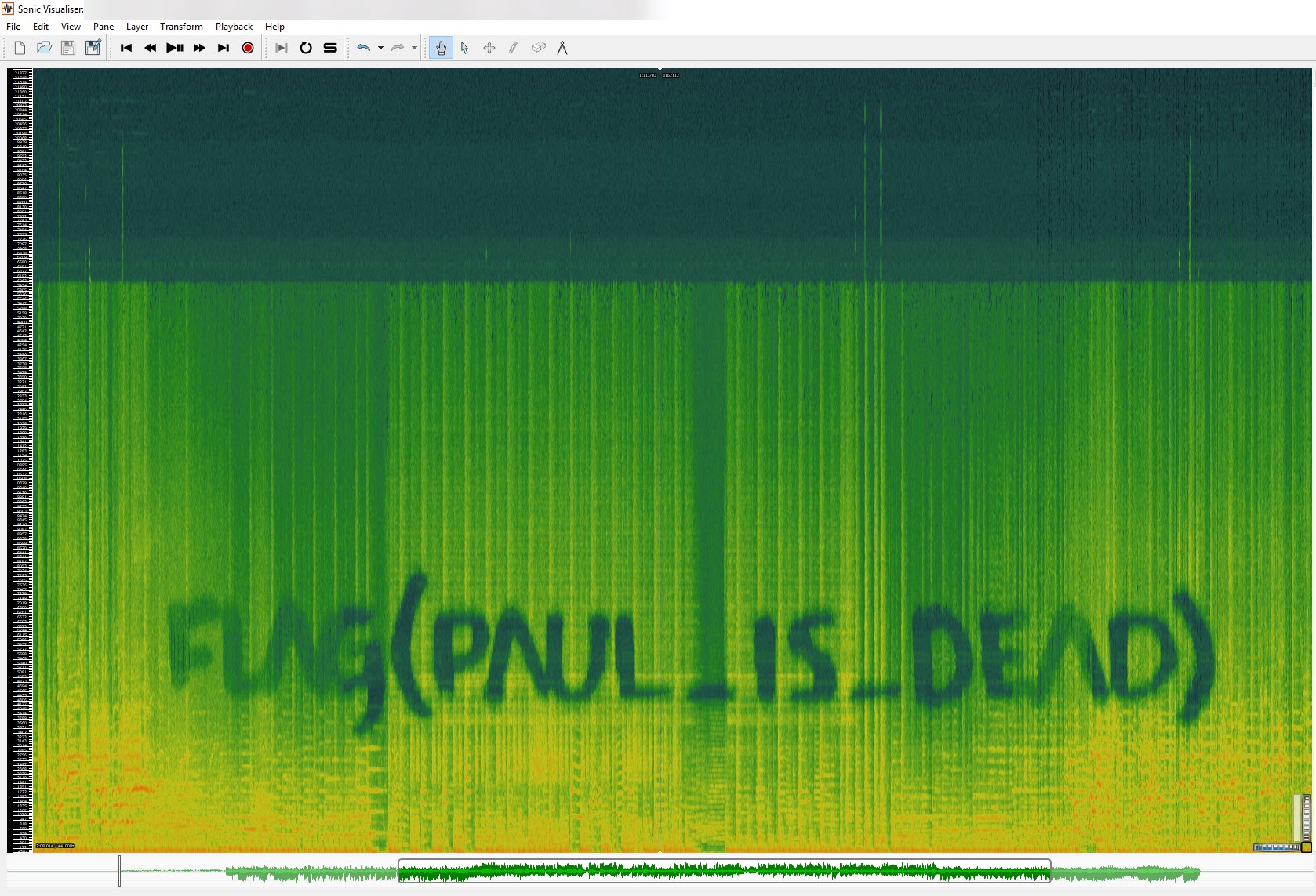
The flag for this task is "paul_is_dead".
Challenge 6
For this task we were presented with a file called "bitrot".
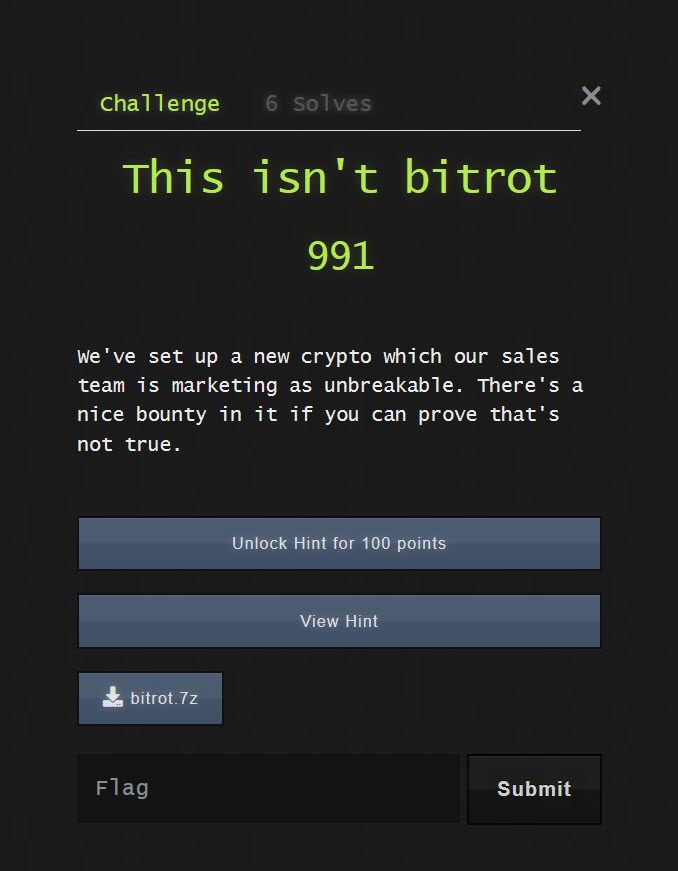
The description for this challenge says that the file isn't bitrot and is (or is not) some kind of crypto. All clues indicated that this might be a message that is encoded using a Caesar cipher, or rot.
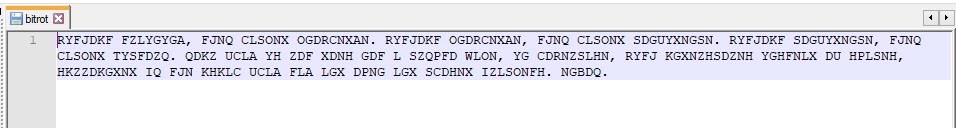
Caesar cipher is a kind of rotation cipher, where each letter is moved a predetermined amount along the alphabet. We tried to decode the message using all forms of ROT1-ROT25. This didn't yield any results. After trying this task for a while, we decided to use 100 points to unlock a hint. As I've never completed a CTF before, I focused on trying to complete the challenges and not worry too much about how many points we received in the end. The hint indicated that this message may be a cryptogram.
Using an online cryptogram solver such as this, we were able to figure out most of the letters to find the hidden message:
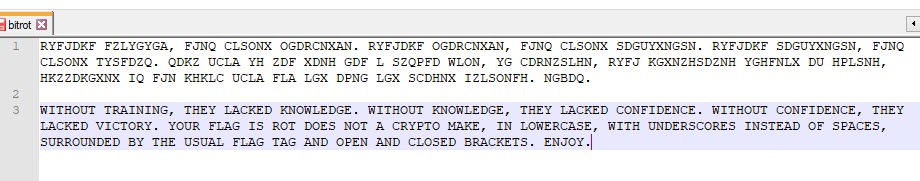
The flag is "rot_does_not_a_crypto_make"
Challenge 7
This is the challenge that I thought would be the hardest. I don't have experience of reversing binary files so I palmed this off (for a while) to my partner in crime @a66ot
The challenge presented us with a file with the extension .SMB
If you open the binary file you will notice that it is a .NES file. This is the format for Nintendo games.
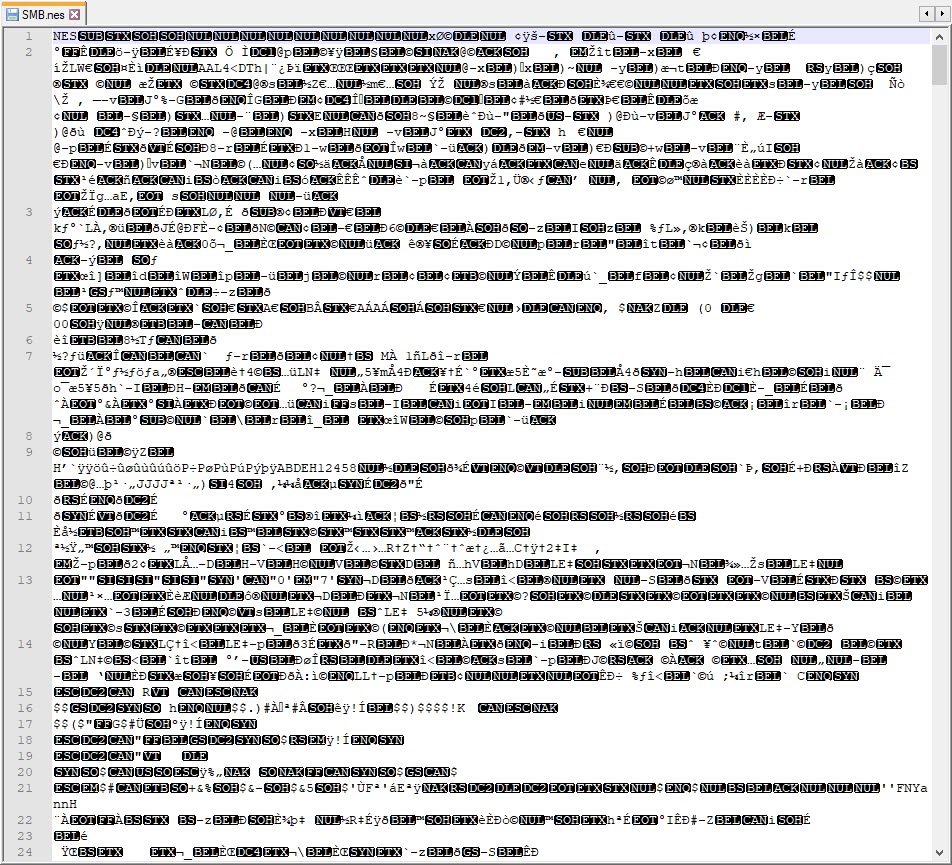
By changing the extension of this file from .SMB to .NES you can open it in a compatible player. I downloaded FCEUX which supports NES emulation. It has a lot of different features which allow you to view in game text, change the colour palette, pause game play and use cheat codes. I opened the game in FCEUX, which showed us that this was the 1985 version of Super Mario Bros.
We knew that something about this game had been changed. The next thing we did was to download the original Super Mario Bros game. We then used HexCMP to compare the two files. Here you can that there is a difference in this part of the binary:
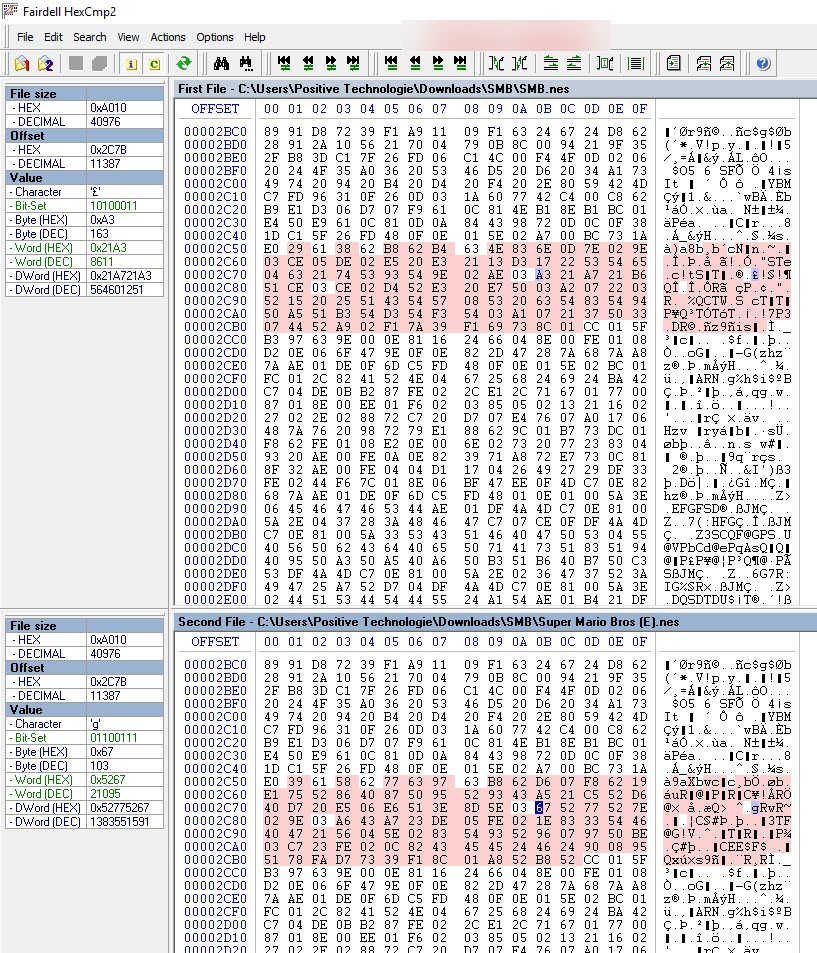
We weren't sure what these offsets were responsible for. We thought there may be a hidden message. Tim (@a66ot) tried to convert the differences to ASCII with the Super Mario symbols table (text.tbl) using a utility called Hexecute. Unfortunately this didn't yield any results. At this point he was out of ideas, and unlocked a hint for 100 points, which read:
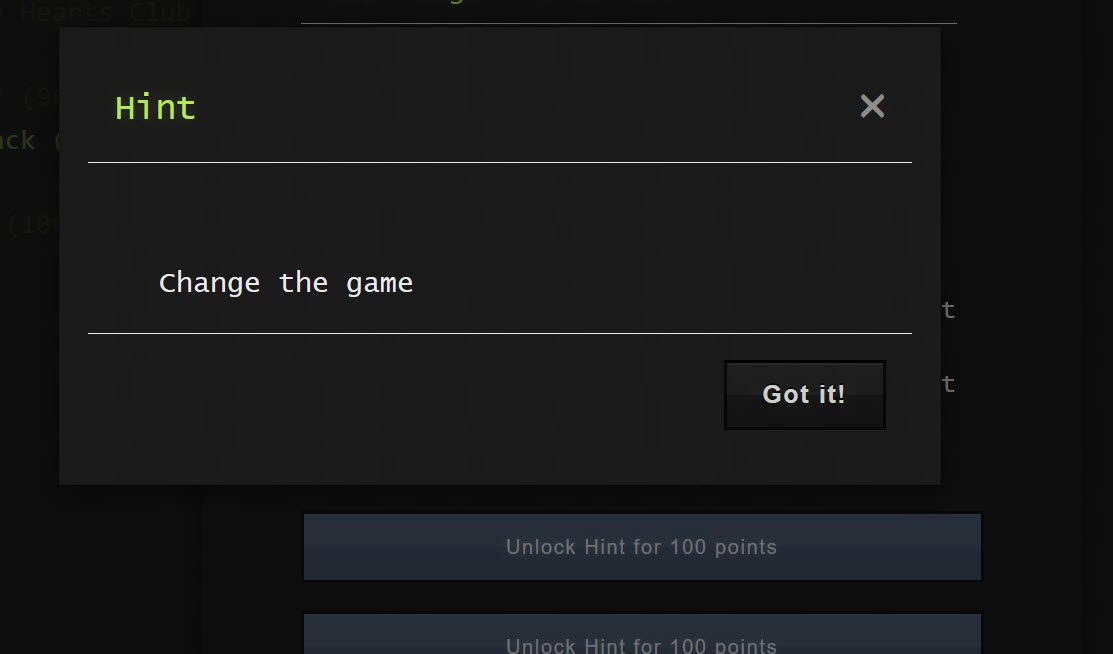
I still thought I'd have no chance figuring out the reverse-engineering task, so I left Tim to it. Instead, I started playing the modified game. Initially dying a lot! But I loved playing the game.

So decided to look up some cheat codes online, adding infinite lives. This allowed me to make it to the second world. Where I hit a wall of breaks that I couldn't pass:
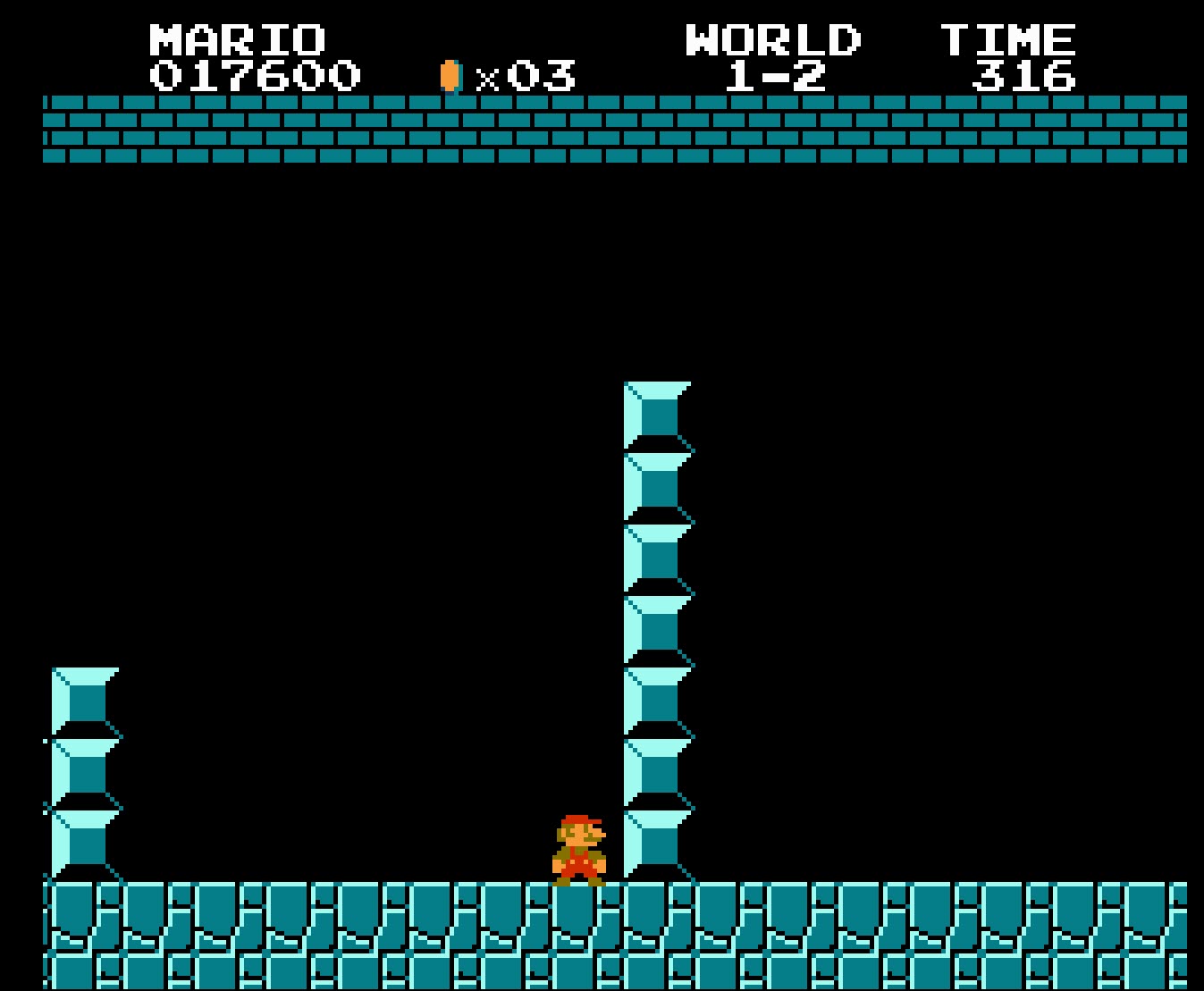
What did I do? Enable another cheat code that allows Mario to do a super jump from a standing start only. Can you spot the flag in the video below?
If you aren't able to view the video, the flag is "sonic".
The Scavenger Hunt is a mix of tasks with fixed points. At this point in the CTF, I realised we had a chance of placing on the scoreboard. We figured we would give the scavenger hunt a go. I believe were the team to complete the most points from this challenge!
Here are the items we had to collect (those tasks which are greyed out are the items we received points for):
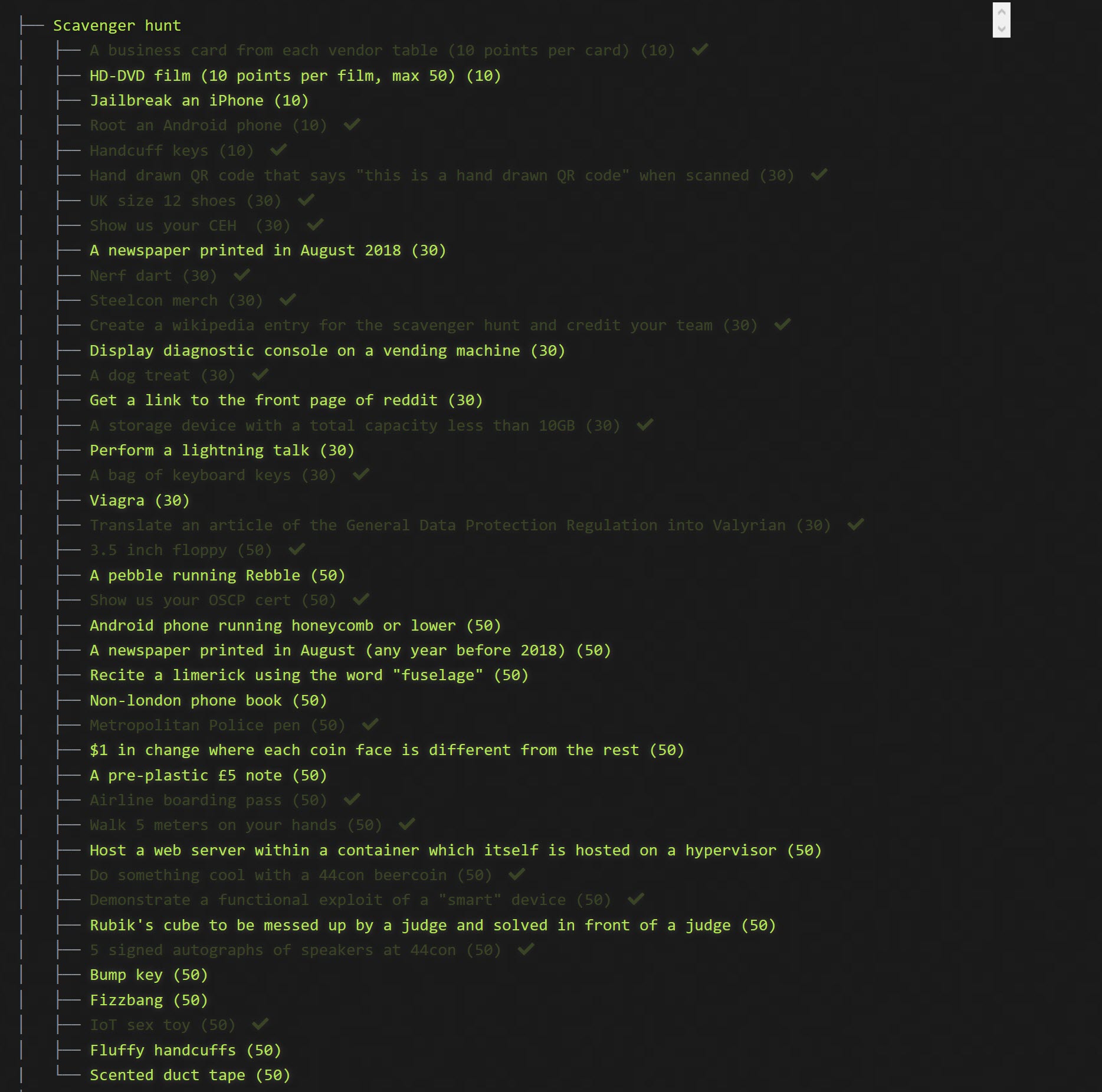
This set of challenges involved interfacing with the real-world!
We made a hand drawn QR code, that read "this is hand drawn QR code"

We found a pair of size 12 shoes, thanks to Adam. We even performed a wheel barrow to complete the "Walk 5 meters on your hands" task. There should be a video of this somewhere on the Interent.
/人◕ __ ◕人\
At the 3pm deadline we had placed 2nd overall. With the leaders "Shadowblokies" taking first by finding the lost wallet (44con challenge).
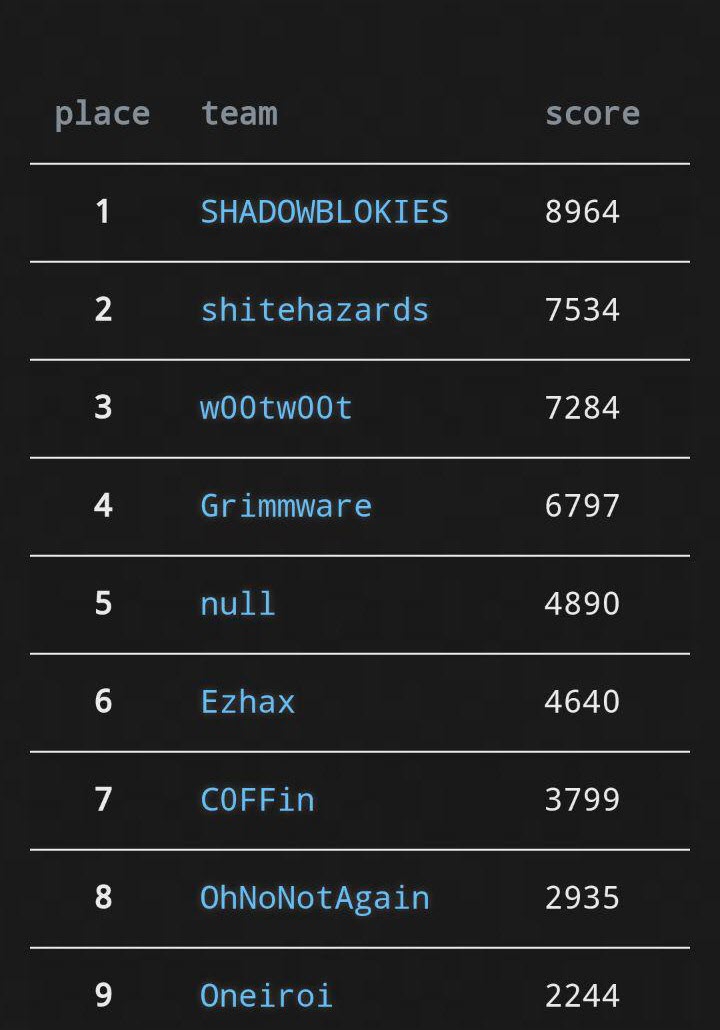
Heres a blurry picture of us collecting our prize:

We won a Nintendo switch courtesy of crowdfense

This was a fantastic first CTF. I had an unbelievable amount of fun and immersed myself in a conference in a way that I've never experienced before. What's even better yet? CROWDFENSE are donating any remaining money to the foodbank.
If you haven't tried a CTF, have a go!