Video - How to buy an ATM - Hacktivity 2017
A video of my talk about the process of buying and hacking an ATM
In April this year whilst roaming the plains of the wild world web, I stumbled across an old Myspace account of mine. Attempting to gain access and delete the account I discovered a business process so flawed it deserves its own place in history. I wrote to Myspace describing my findings and the impact.
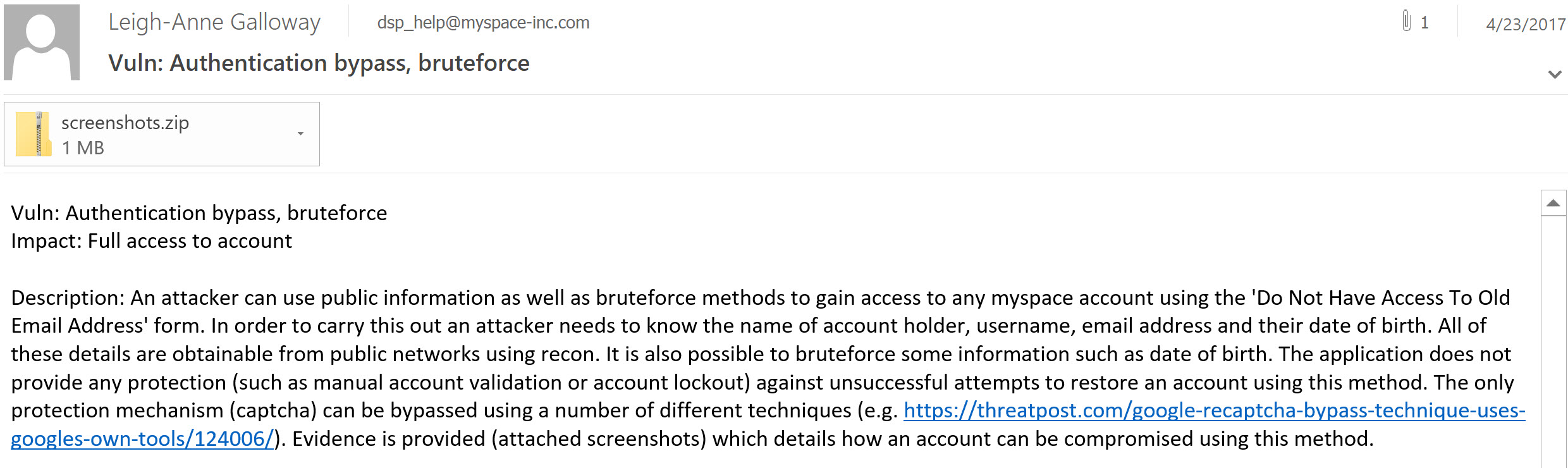
After almost three months I received almost no response from Myspace, except an automated one.
During my preparation for this article, I realised that the vulnerability is even worse than I had first thought. This vulnerability allows anyone access to any Myspace account, with only three pieces of information.
Myspace may no longer be relevant as a social media site, but its treatment of security is as relevant as ever. To understand how Myspace got to this state, let’s start at the beginning.
Close your eyes for a minute. Let’s take a journey through data breach history. Try to imagine a time when Facebook and Twitter weren’t the top social media websites in use. Go back a bit further, way back and you’ll arrive in a year called 2006.
2006 was the year that Apple released the MacBook. It was the year that LOLcats.com was registered as a domain. In 2006 everyone was using Myspace to communicate with each other. Now scroll forward a few years to 2009. Myspace wasn’t looking so shiny. The world had begun to move on, everyone was emigrating to the new platform called Facebook.
Flash forward to the year 2016. It emerged that Myspace had (historically none the less) suffered one of the largest breaches in history. The details of 360 million Myspace user accounts were made available online. Myspace released a response on their blog dating the compromised accounts to prior to 2013.
No worries, they said “we have invalidated all user passwords for the affected accounts created prior to June 11, 2013 on the old Myspace platform”.
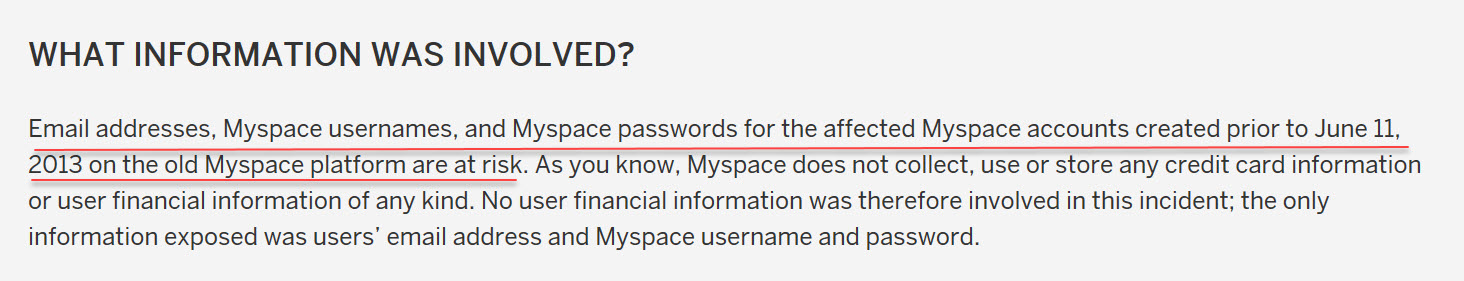
Great so only accounts used on the old platform were affected. Myspace assured us that they take security seriously “We have several dedicated teams working diligently to ensure that the information our members entrust to Myspace remains secure.”

But wait, there’s more! Myspace told us “We are currently utilizing advanced protocols including double salted hashes”

Double salted hashes sound great, right? Double hashed passwords should, in theory mean that it takes an attacker more effort to guess passwords.
The trouble with theory is that it often works quite differently in practice. So differently in this case that you don’t actually need a password. You can access any, yes, any Myspace account with only three pieces of information.
I first stumbled on this vulnerability whilst trying to close my account. Myspace were kind enough to implement an account recovery feature, which looks like this:
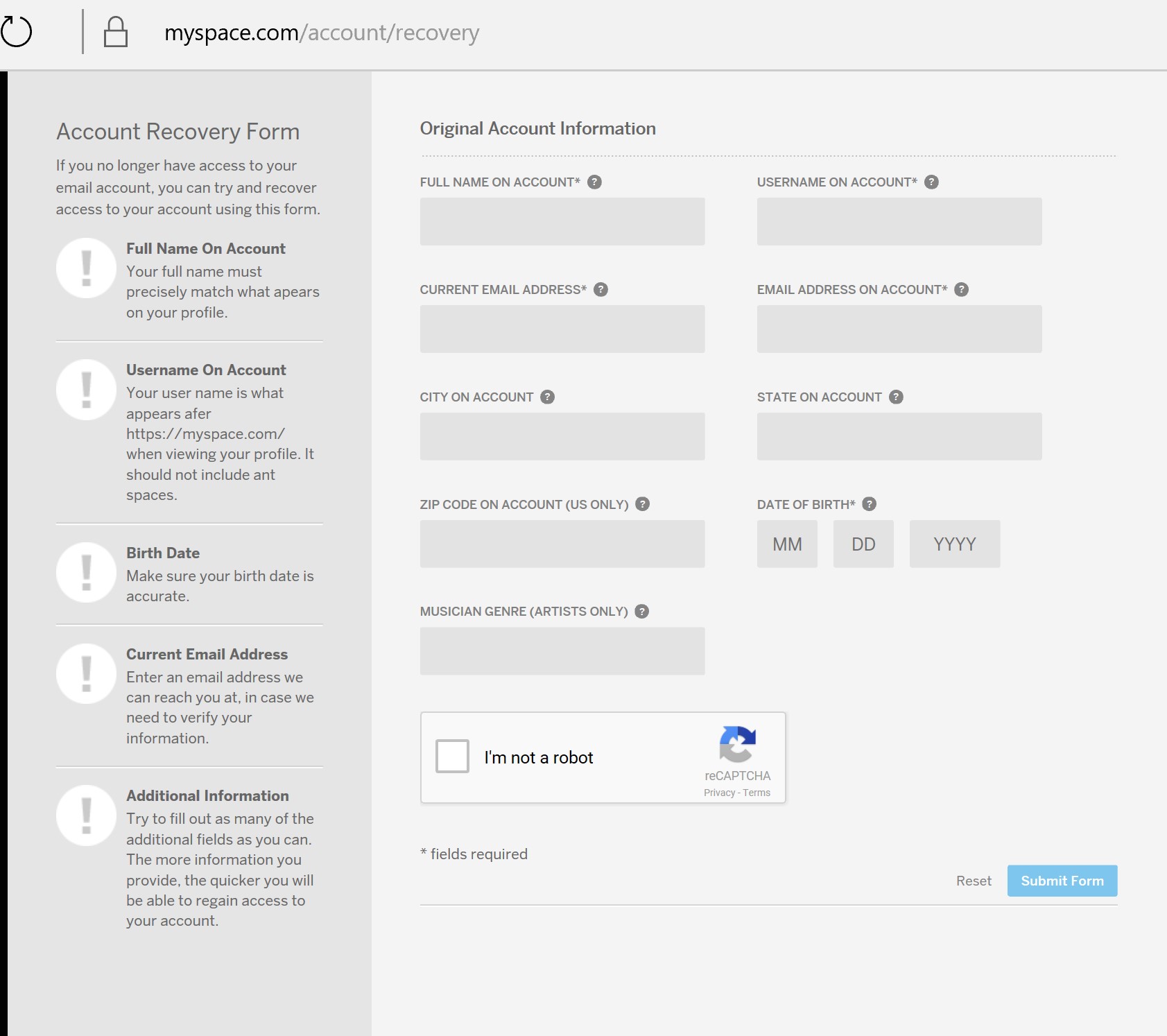
I completed the account recovery form assuming that the request would be forwarded to a human who would verify my identity before assisting me in recovering my account. After all Myspace takes security very seriously, right?
To my surprise I was given full access to my account immediately!
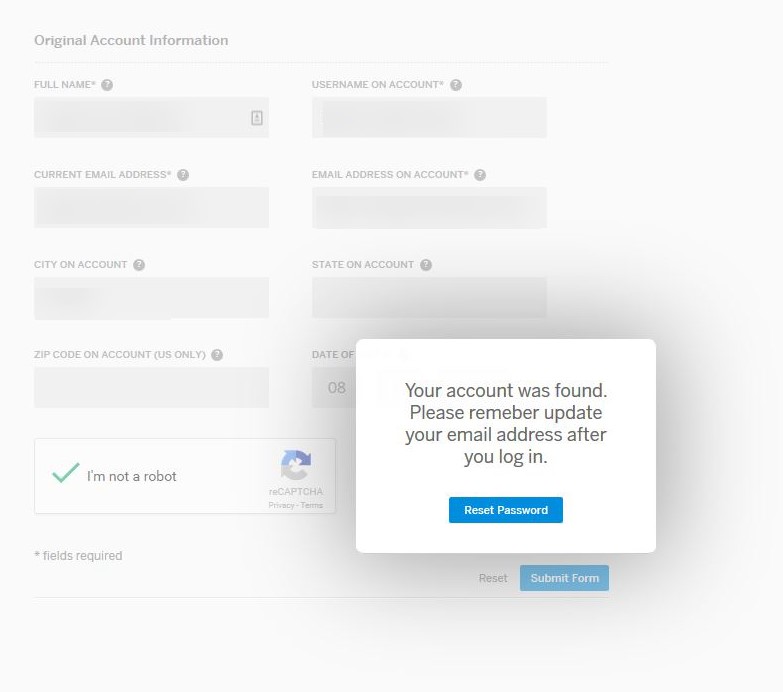
Myspace then forwards you to a reset password page and kindly reminds you to update any other information associated with your account. Well that’s pretty bad right? It gets even more interesting.
Take a step back to that account recovery page, let’s take a closer look. Notice the “*” indicating the minimum required information to recover your account. This is listed next to name, username, current email address, email address on account and date of birth. Secondly note the message in the bottom left corner which says “Try to fill out as many of the fields as you can. The more information you provide, the quicker you will be able to regain access to your account.”
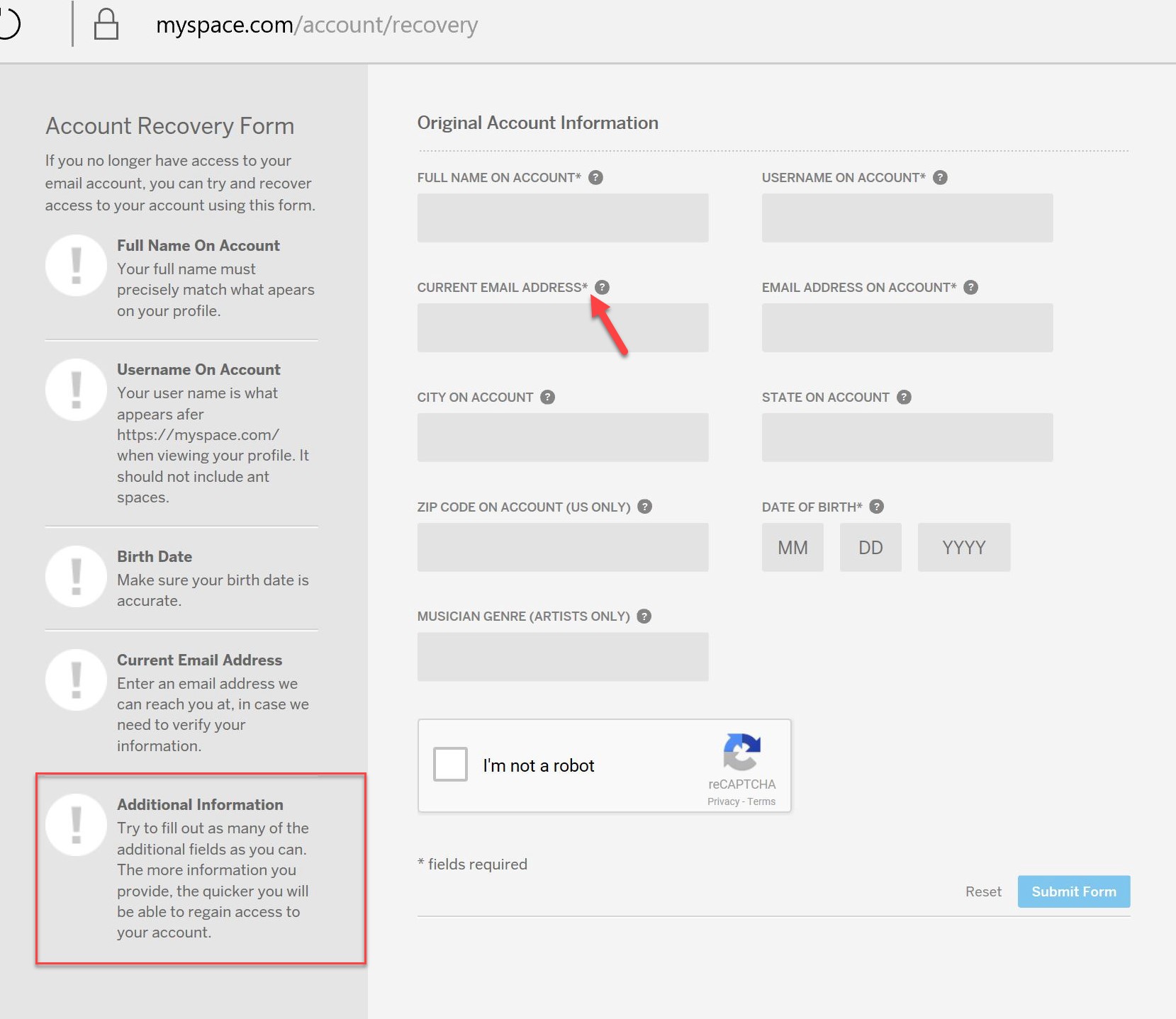
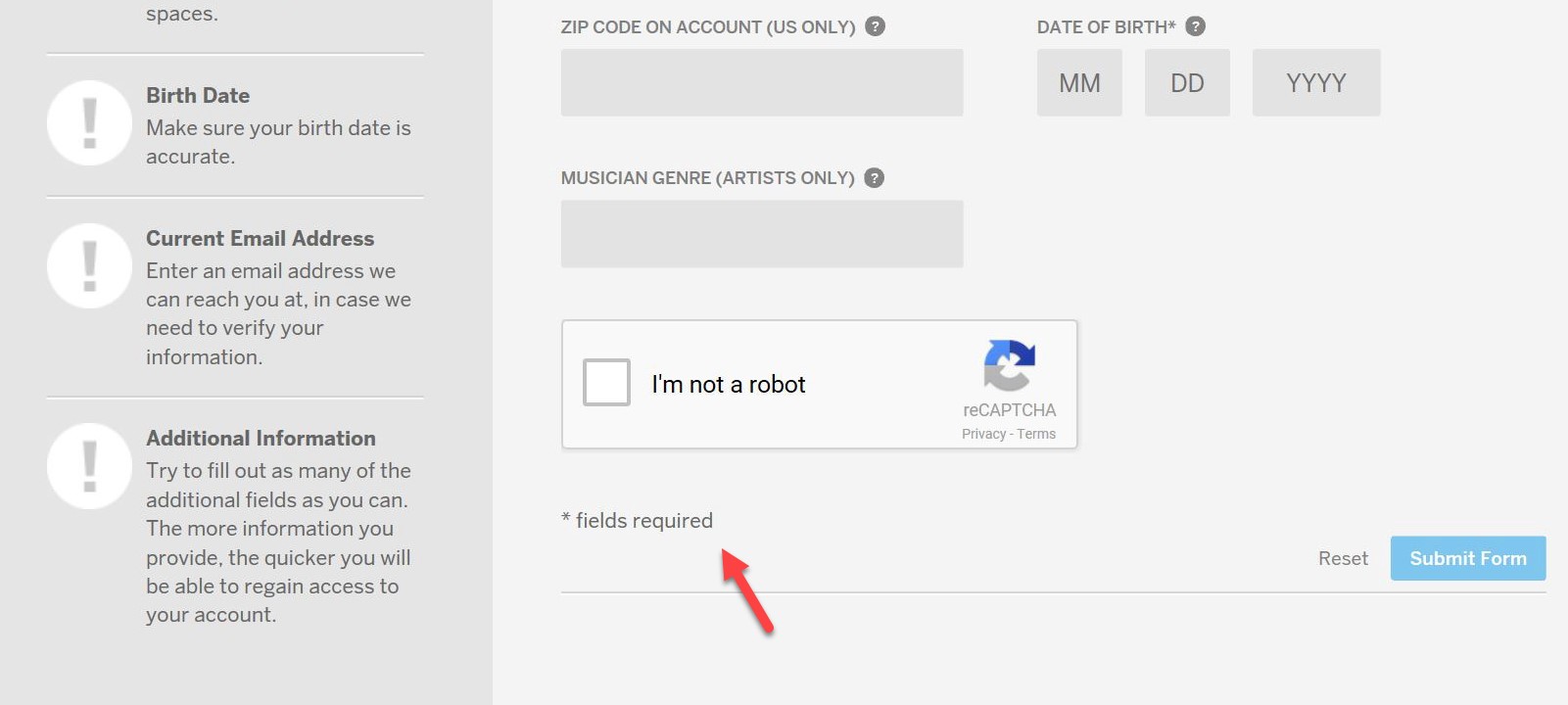
These seem like conflicting messages to me, but I assume Myspace are referring to the additional fields like city or state. All fields marked with an “*” are required fields, aren’t they?
Let’s see if Myspace validates the existing email address associated with the account. Here’s the current email address “123453455@gmail.com”.
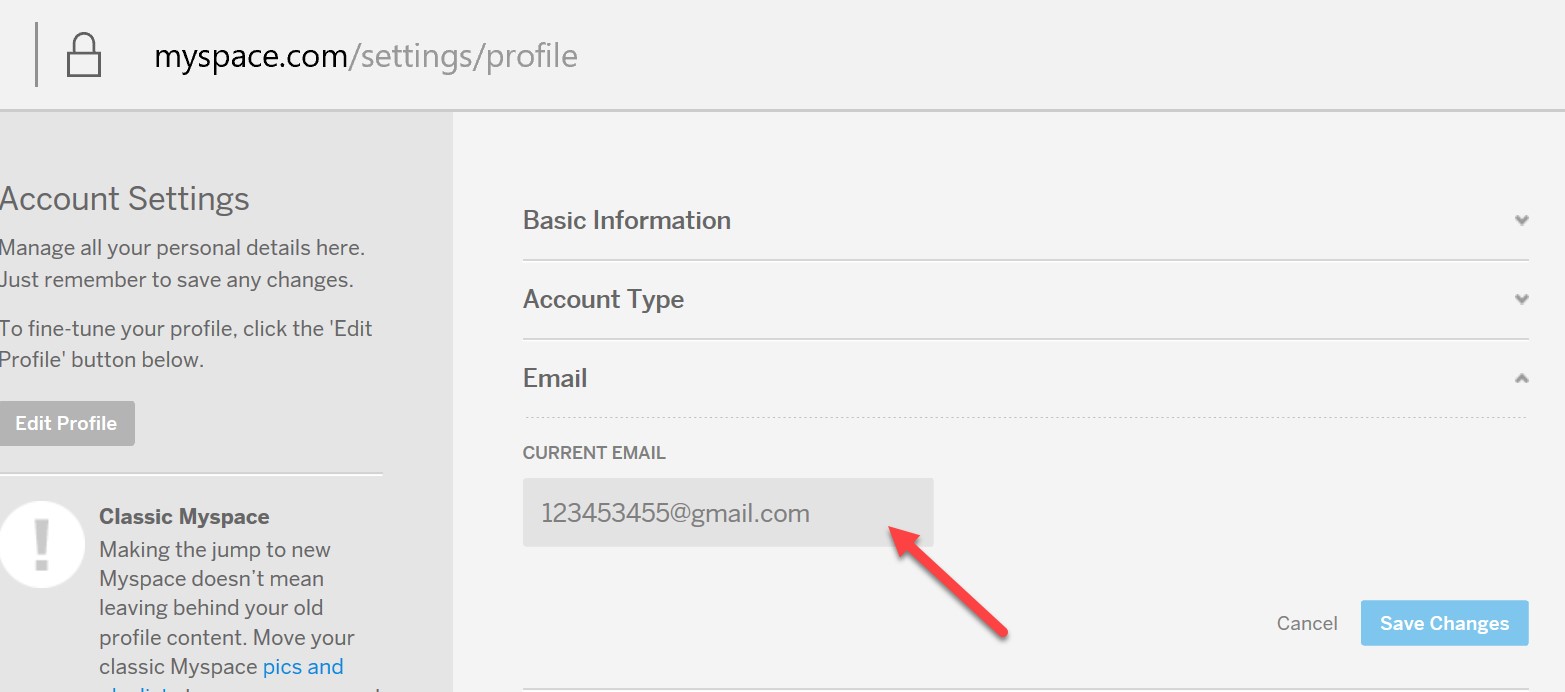
Let’s go back to the account recovery form and fill in a fake email
address “email@whateveremail.com”.
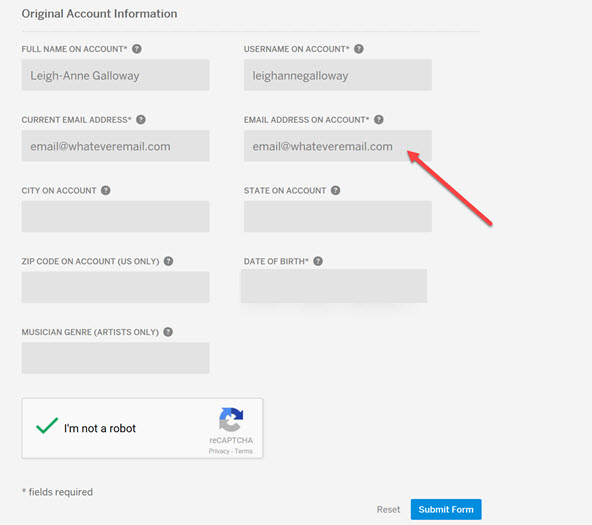
Success! it turns out some of those fields aren’t required at all. Myspace doesn’t validate email addresses.
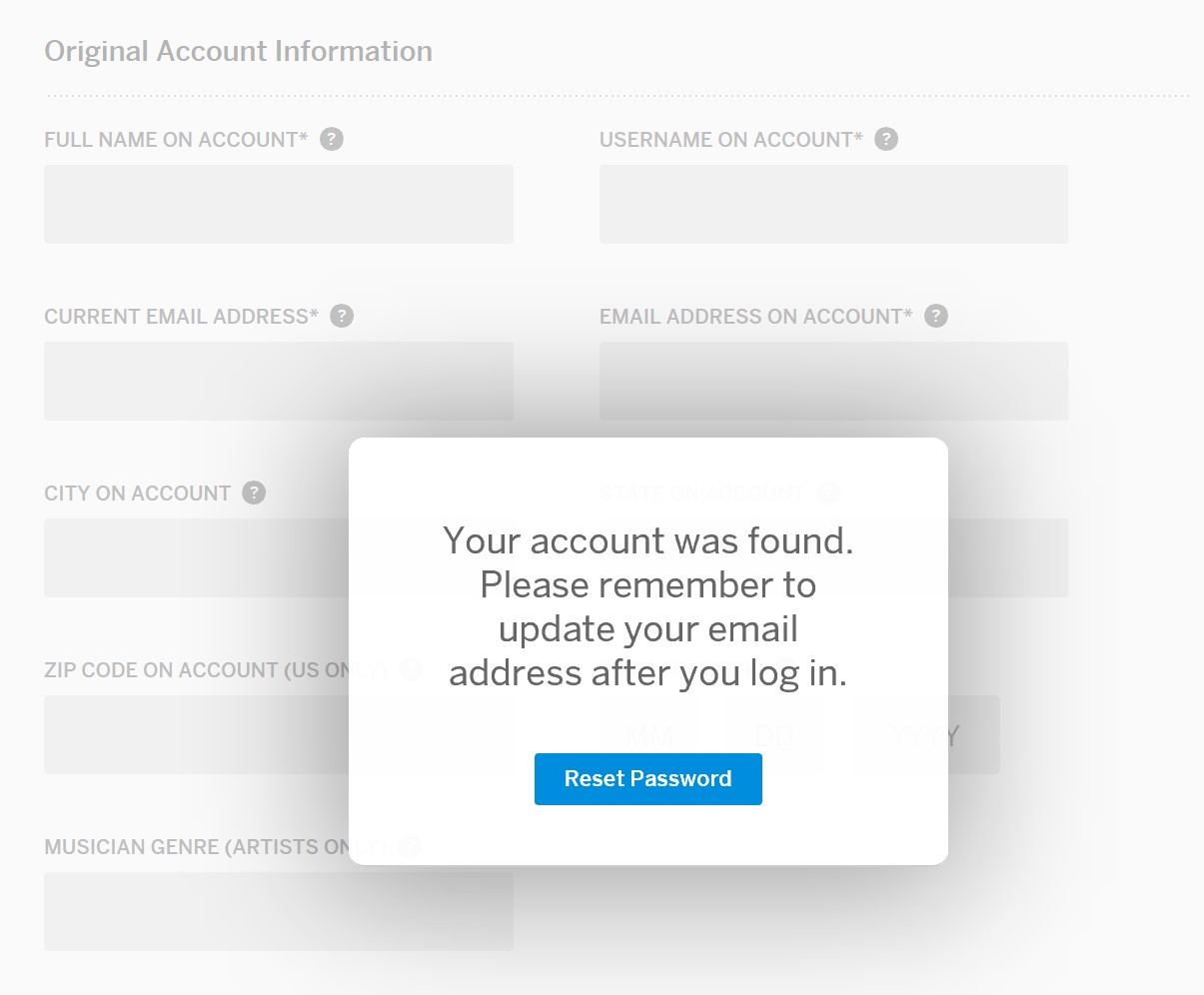
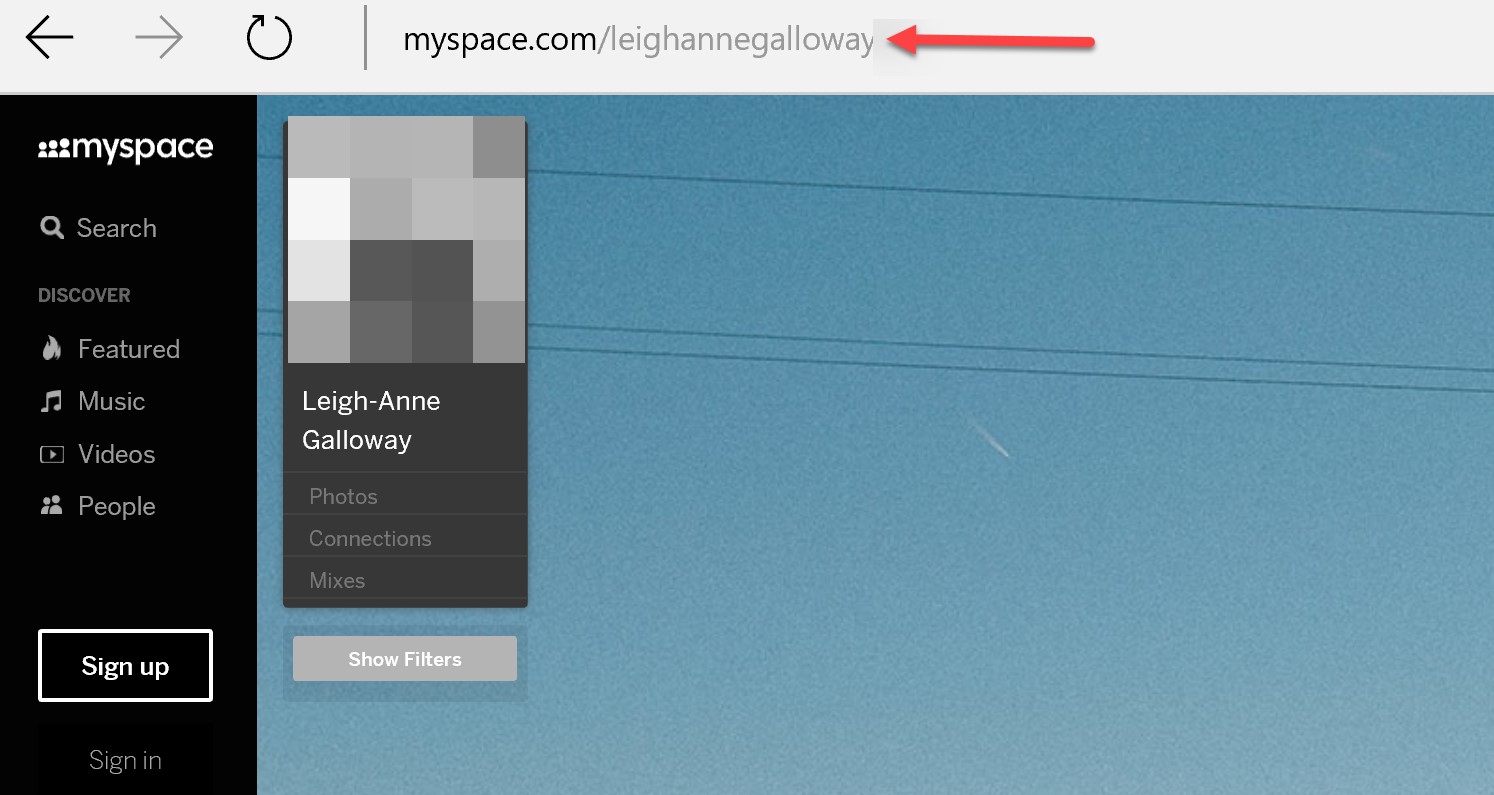
Myspace only validates name, username and date of birth. The full name and the username of the account holder can be found from a simple google. Username is located in the profile url, and name is located on the profile page:
Date of birth is probably the hardest of all three to obtain, but not impossible.
The good news is that you can remove your account completely. If you can’t remember all account details the first step is to go through the account recovery that I went through above. After that, select account settings:
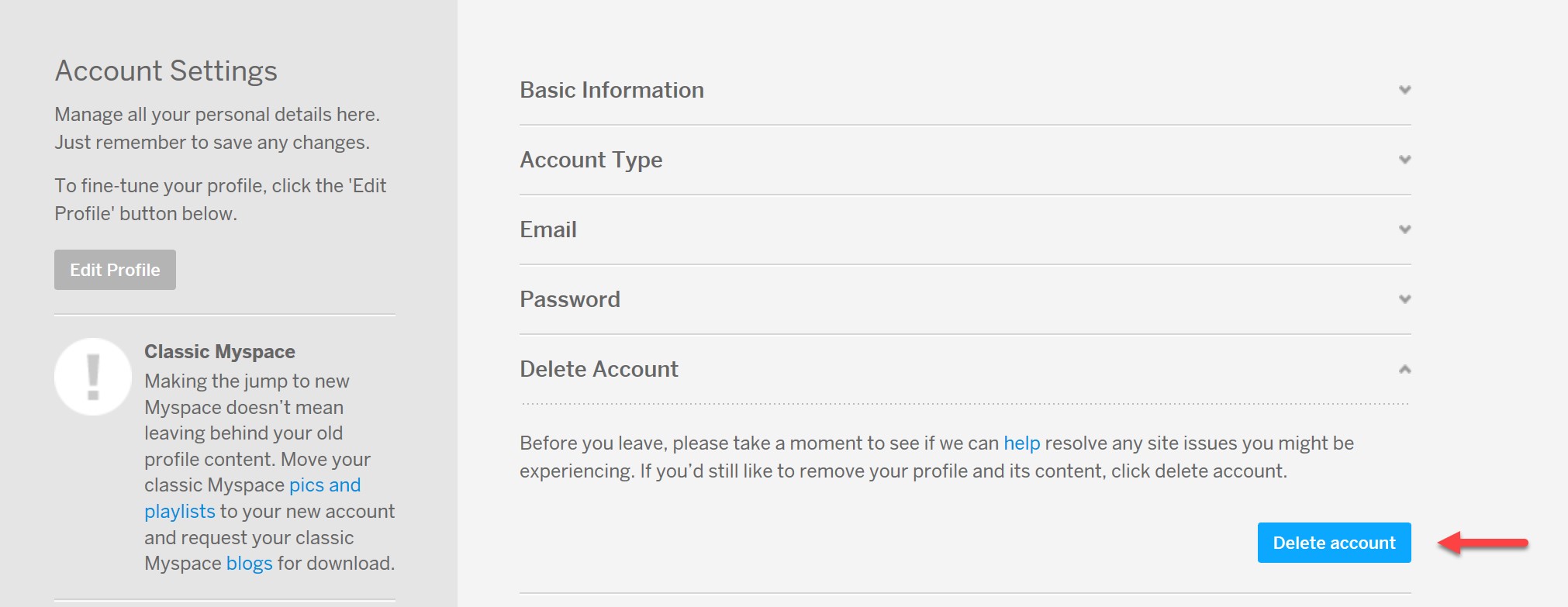
You’ll find the delete account option below:
For a video demonstrating just how easy this is:
So how seriously does Myspace take security? Not seriously at all. I sent an email to Myspace in April documenting this vulnerability and received nothing more than an automated response. This has lead me to disclose the vulnerability while it still exists. It seems Myspace wants us all to take security into our own hands. If there is a possibility that you still have account on Myspace, I recommend you delete your account immediately.
Perhaps this situation is not surprising as most of us no longer use Myspace. So why does this matter? Myspace is an example of the kind of sloppy security many sites suffer from, poor implementation of controls, lack of user input validation, and zero accountability. Whilst Myspace is no longer the number one social media site, they have a duty of care to users past and present.